Stream-to-Splunk Encryption
Encrypt at Ingest-Time and Decrypt in Splunk
With Cribl Stream, you can encrypt your sensitive data in real time before it’s forwarded to and stored at a destination. Using the out-of-the-box Mask function, you can define patterns to encrypt with specific key IDs or key classes. To decrypt in Splunk, you will need to install Cribl App for Splunk on your search head. (The app will default to mode-searchhead.)
Keys and Key Classes
Symmetric encryption keys can be configured through the CLI or the UI. They’re used to encrypt the patterns, and users are free to define as many keys as required.
Key classes are collections of keys that can be used to implement multiple levels of access control. Users (or groups of users) that have access to data with encrypted patterns can be associated with key classes. You can use these classes to provide more-granular access rights, such as read versus decryption permissions on a dataset.
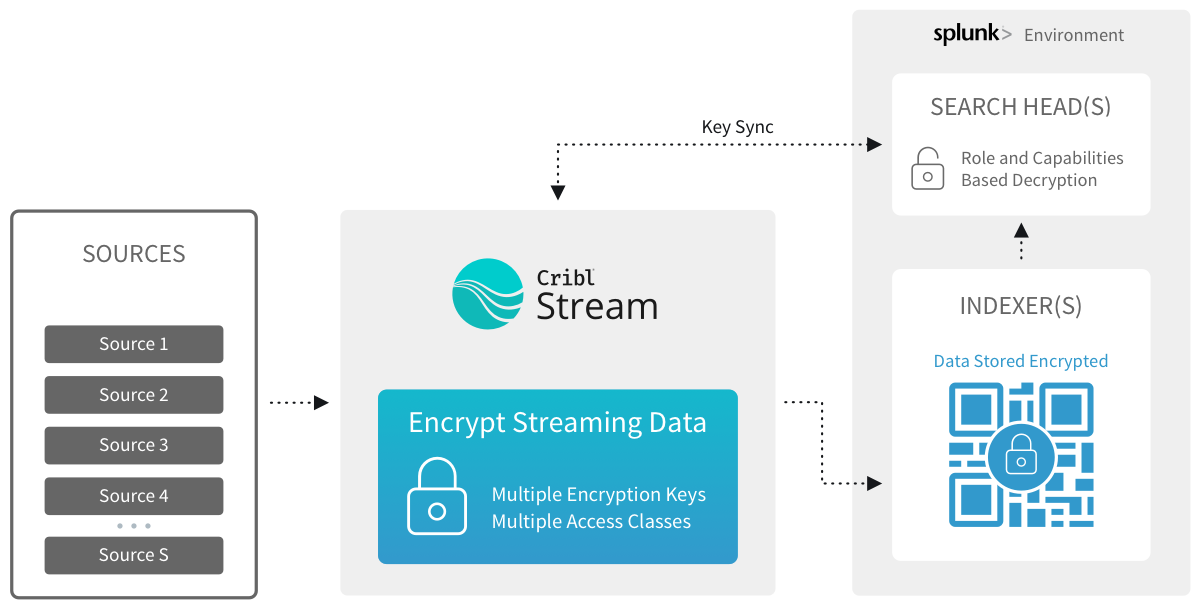
Encrypt in Cribl Stream and Decrypt in Splunk
Define one or more keys and key classes on Cribl Stream. (See UI- and CLI-based instructions.)
Sync
authwith the decryption side (Splunk Search Head). (The Splunk-side directory is$SPLUNK_HOME/etc/apps/cribl/local/cribl/auth/.)Apply the Mask function to patterns of interest, using C.Crypto.encrypt().
Decrypt on the Splunk search head, using Role-Based Access Control on the
decryptcommand.
Examples
Encryption Side
You can generate keys via the UI or the CLI.
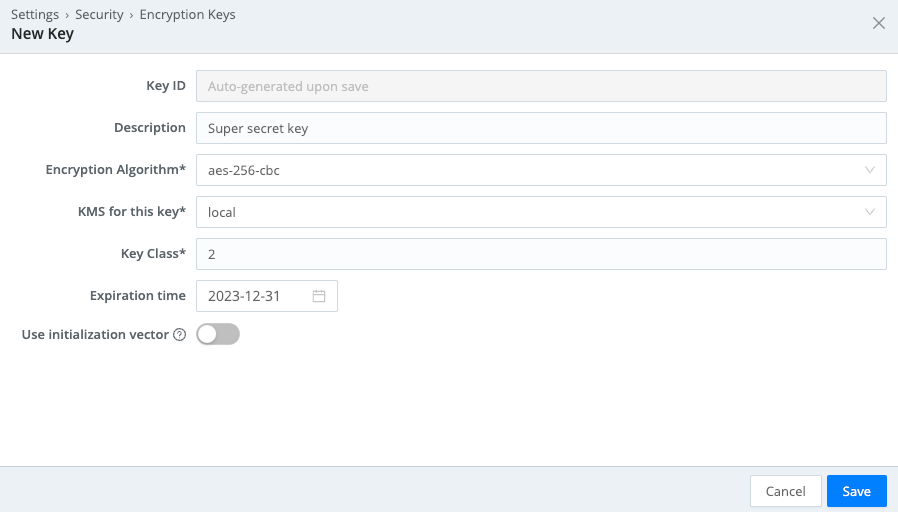
To generate keys via the UI, access Group Settings > Security > Encryption Keys:
To generate one or more keys via the CLI, pattern your commands after these examples.
In a single-instance deployment:
$CRIBL_HOME/bin/cribl keys add -c 1 -i
...
$CRIBL_HOME/bin/cribl keys add -c <N> -i
In a distributed deployment, to generate keys on a Worker Group named uk:
$CRIBL_HOME/bin/cribl keys add -c 1 -i -g uk
...
$CRIBL_HOME/bin/cribl keys add -c <N> -i -g uk
Add -e <epoch> to the above commands if you’d like to set expiration for your keys.
For all command/syntax options, see Adding Keys.
Decryption Side
- Download the Cribl Stream App for Splunk from Cribl’s Download Cribl Stream page: In the Select Release Version dropdown, select the Cribl App for Splunk option.
To install the Cribl Stream App for Splunk on your search head, untar the package into your
$SPLUNK_HOME/etc/appsdirectory. The app will default tomode-searchhead.Assign permissions to the
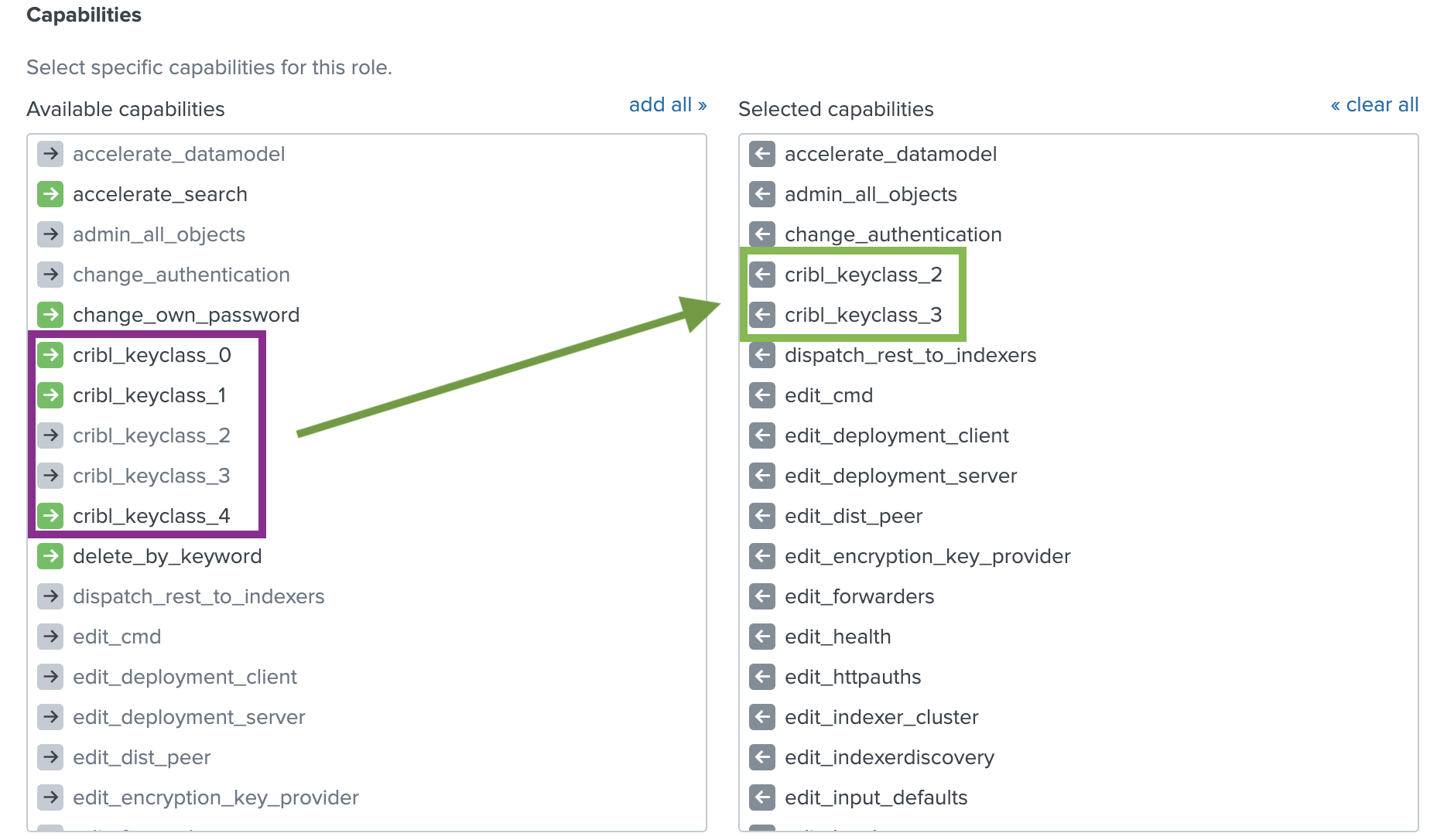
decryptcommand, per your requirements.Assign capabilities to your Roles, per your requirements. Capability names should follow the format
cribl_keyclass_N, whereNis the Cribl Key Class. For example, a role with capabilitycribl_keyclass_1has access to all key IDs associated with key class1. You can use more capabilities, as long as they follow this naming convention.
In the
$SPLUNK_HOME/etc/apps/cribl/local/cribl/auth/directory, synccribl.secret|keys.json. (To successfully decrypt data, thedecryptcommand will need access to the same keys that were used to encrypt, in the Cribl instance where encryption happened.)In a single-instance deployment, the
cribl.secretandkeys.jsonfiles reside in:$CRIBL_HOME/local/cribl/auth/.In a distributed deployment, these files reside on the Leader Node in:
$CRIBL_HOME/groups/<group-name>/local/cribl/auth/.When using Cribl Stream’s UI, you can download these files by clicking Get Key Bundle.
Sync/copy these files over to their counterparts on the search head (decryption side). In a non-Splunk integration, you would copy these assets to wherever decryption will take place.
Modifying Keys
When you update keys by editing the
keys.jsonfile, you must add them back to the directories above (respectively, on a single instance or on a distributed deployment’s Leader Node).
Usage
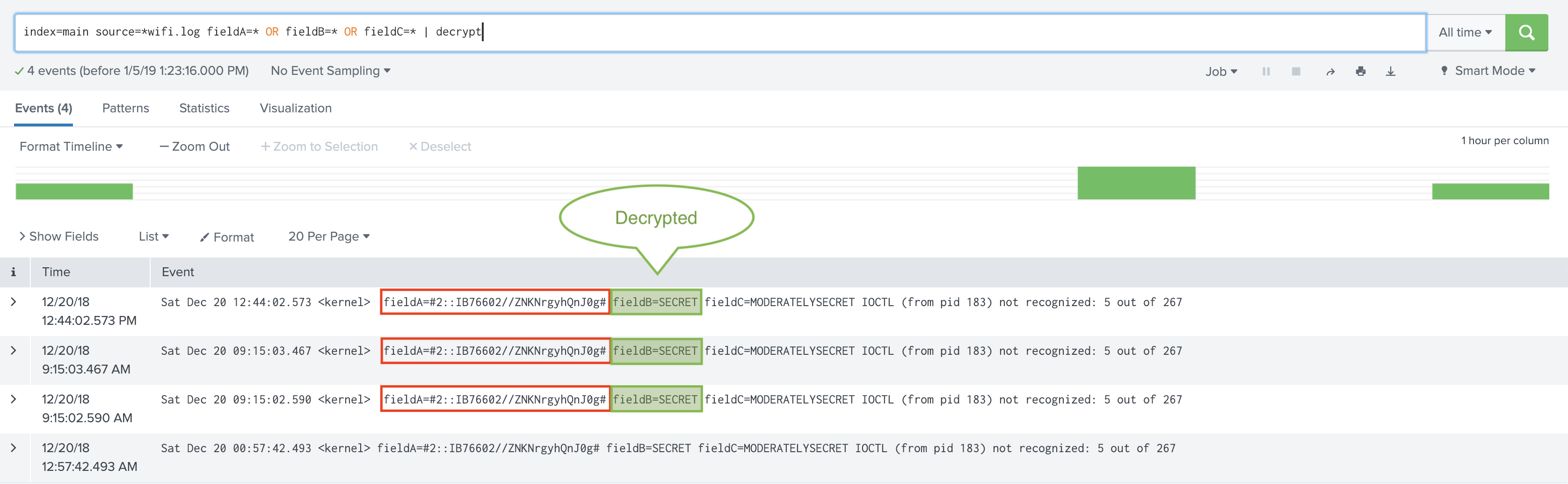
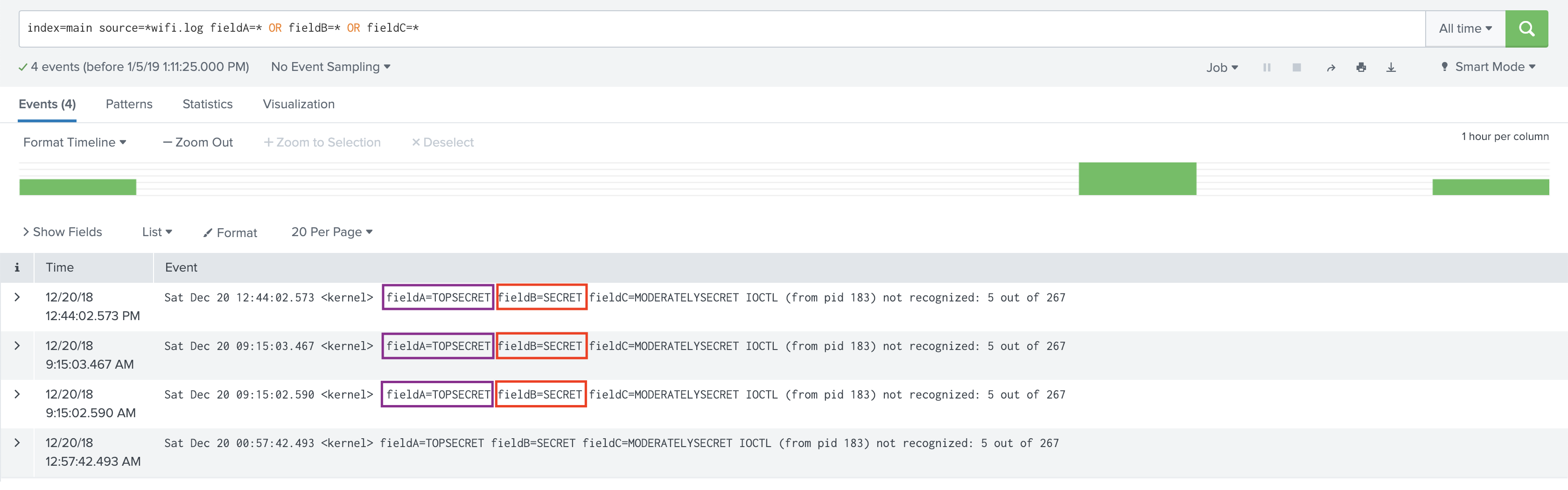
Before Encryption: Sample un-encrypted events. Notice the values of fieldA and fieldB.
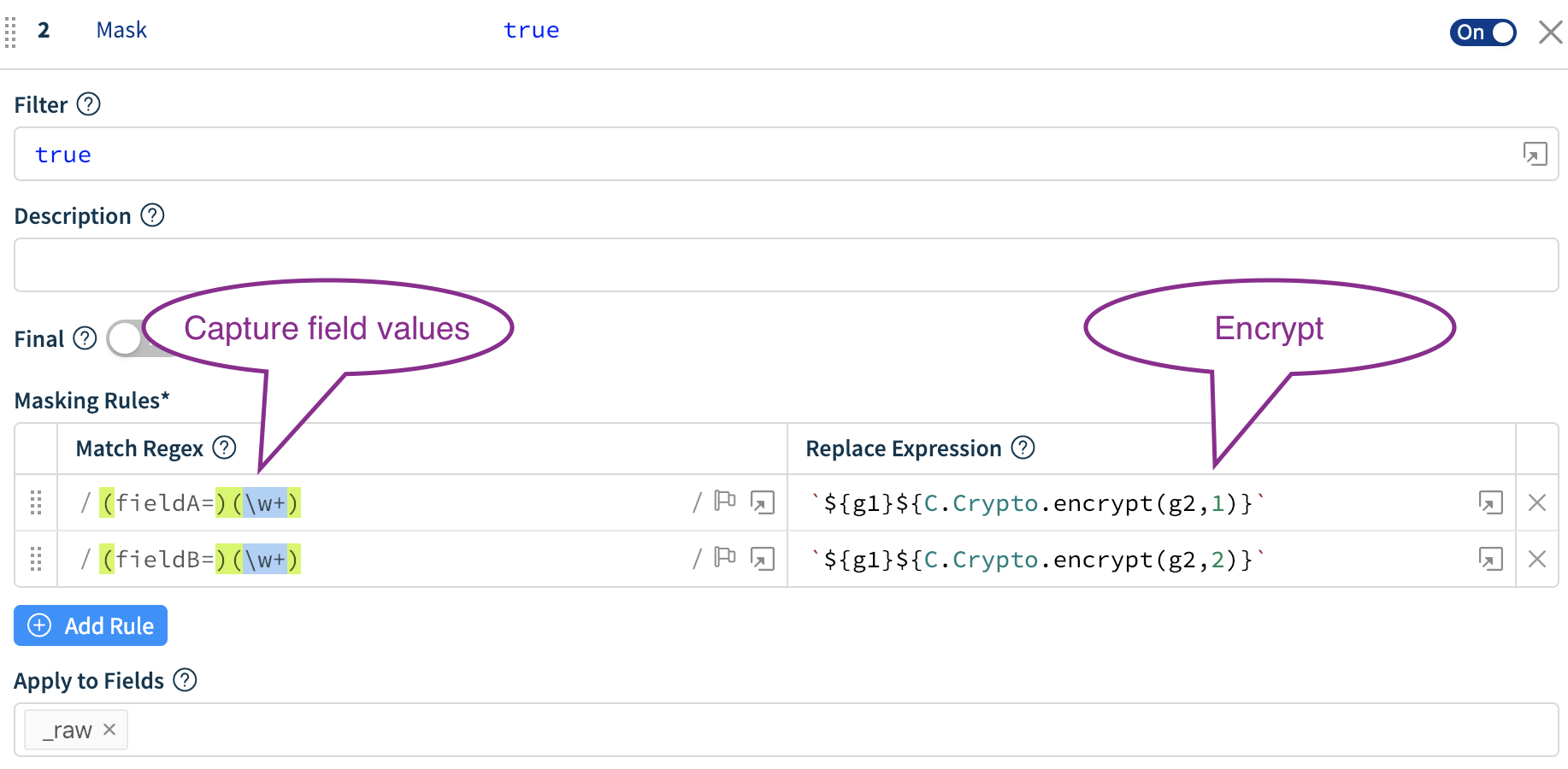
Next, encrypt fieldA values with key class 1, and fieldB with key class 2.
After Encryption: again, notice the values of fieldA and fieldB.
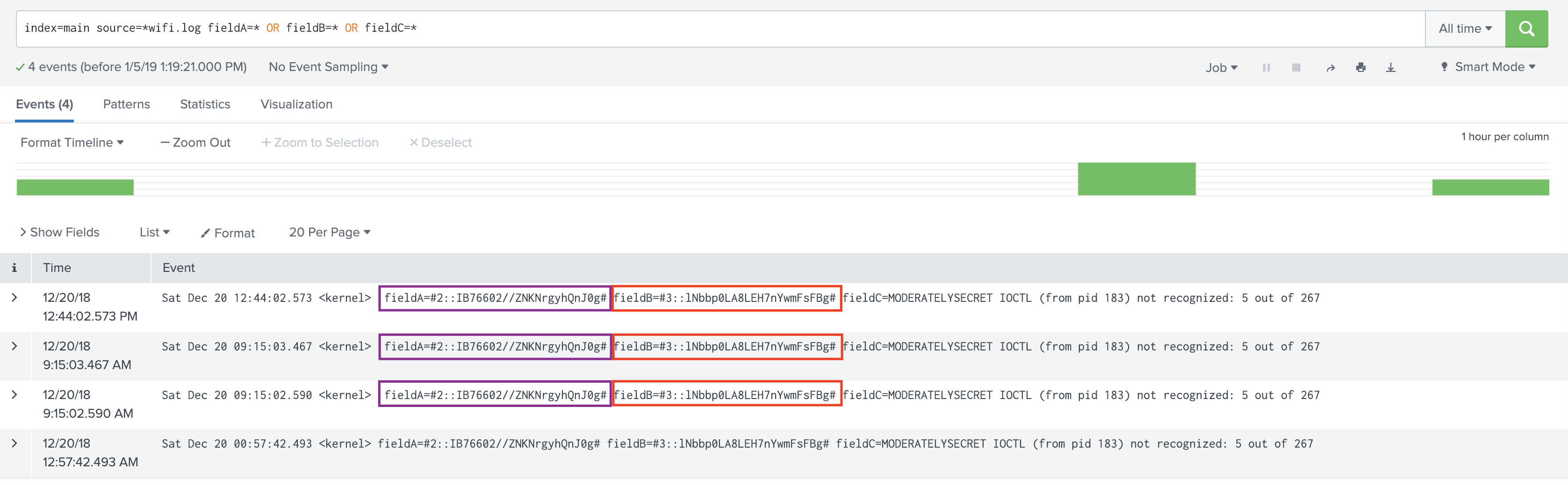
Here, we’ve decrypted fieldB but not fieldA. This is because the logged-in user has been assigned the capability cribl_keyclass_2, but not cribl_keyclass_1.