These docs are for Cribl Edge 4.1 and are no longer actively maintained.
See the latest version (4.16).
SAML/Okta Setup Examples
This example uses Okta as the identity provider (IDP).
Get URL and ID from Cribl
Cribl will provide the following information about your Cribl.Cloud Organization, to include in the SAML application that you create in your IDP:
Assertion Consumer Service URL.
Okta calls this a “Single sign-on URL,” and this is the first of two URLs that your Cribl Organization’s SSO > SAML tab lists under the same label. Example:
https://login.cribl.cloud/login/callback?connection=<$organizationID>Test SSO URL.
Required to test your connection. Okta accepts this under “Other Requestable SSO URLs,” and this is the second URL that your SSO > SAML tab lists under “Single sign-on URL.” Example:
https://<$organizationID>.cribl.cloud/api/assertEntity ID.
Okta calls this an “Audience URI (SP Entity ID),” and your SSO > SAML tab calls it just an “Audience URI.” Example:
urn:auth0:cribl-cloud-prod:<$organizationID>
Create SAML 2.0 App Integration
Using Okta as our example, create a SAML app integration. Start here:
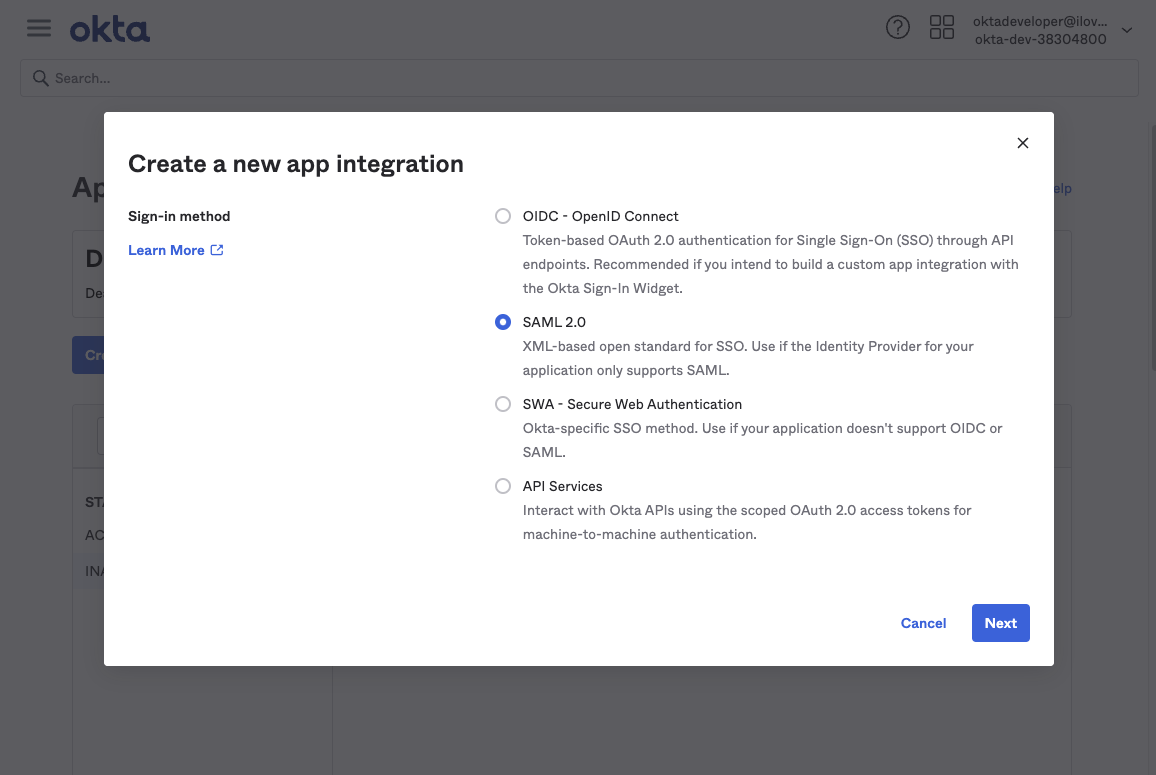
Next, create the app integration with Sign-in method: SAML 2.0.
Configure SAML Settings
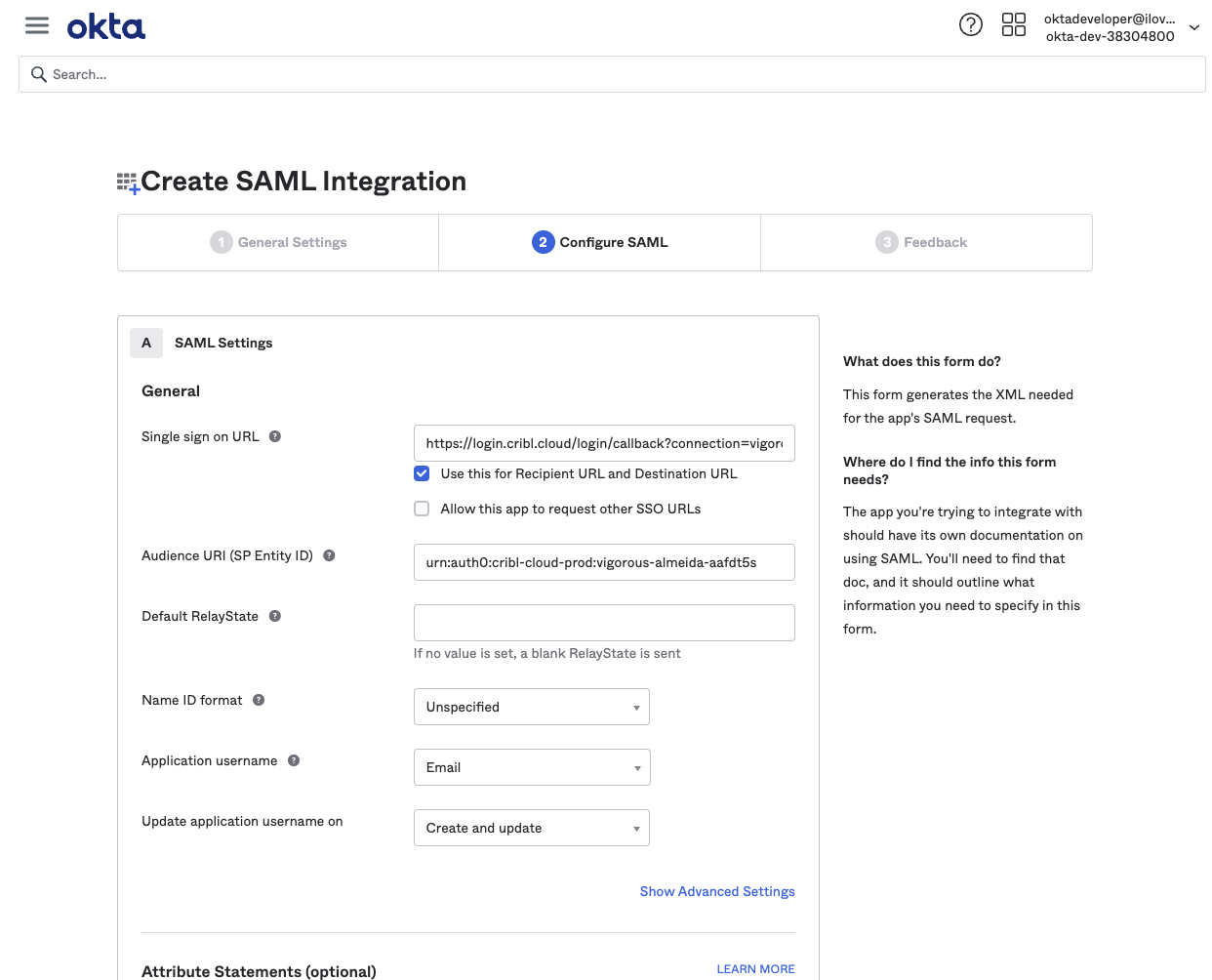
In the app integration SAML Settings section, configure the following options.
Single sign-on URL (Assertion Consumer Service URL):
https://login.cribl.cloud/login/callback?connection=<$organizationID>Audience URI (SP Entity ID):
urn:auth0:cribl-cloud-prod:<$organizationID>Application username:
EmailThe
nameidentifierassertion in SAML responses must be the user’sEmail.
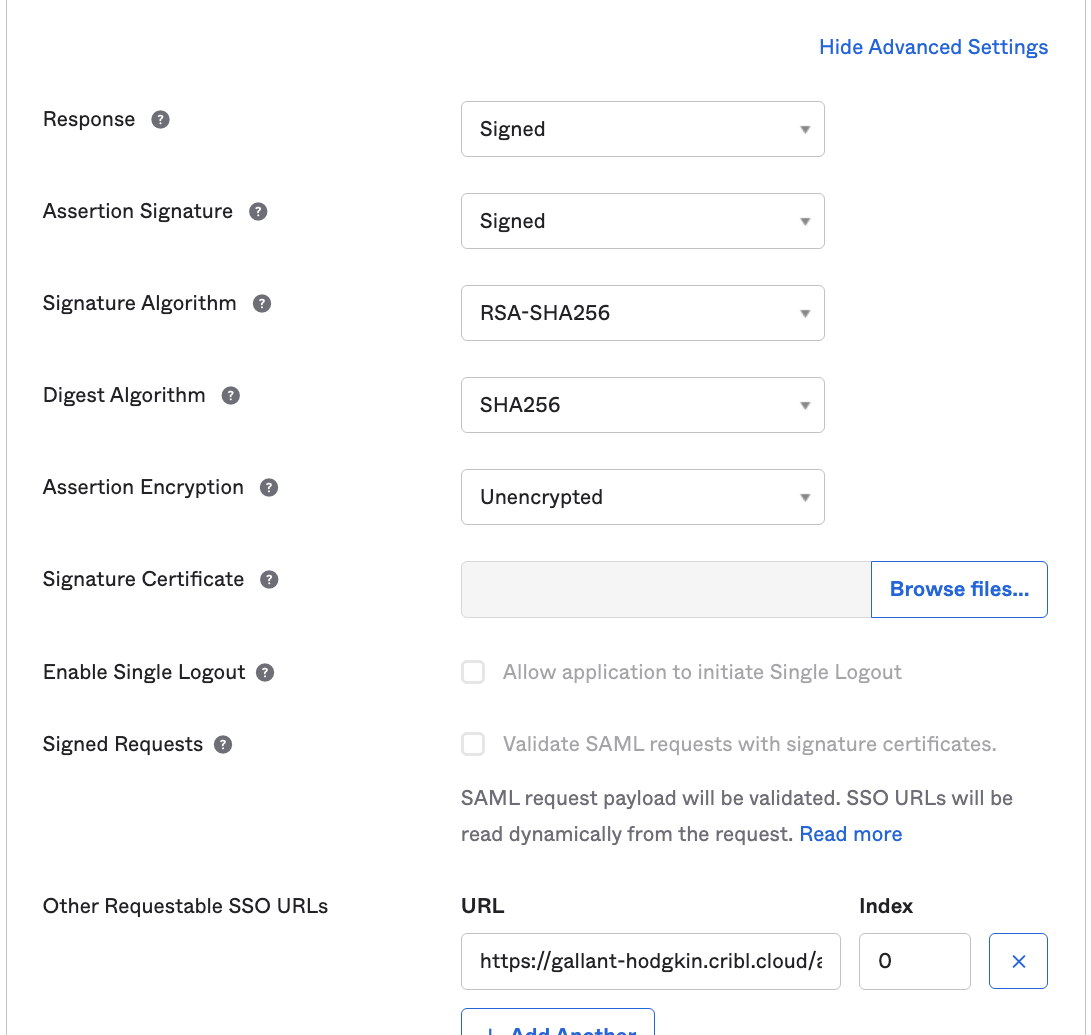
Next, click the SAML Settings section’s Show Advanced Settings link. Then navigate down to configure a single row of Other Requestable SSO URLs, as follows:
URL: From your Cribl.Cloud Organization’s SSO > SAML tab, this is the second Single sign-on URL. It will be in this format:
https://<$organizationID>.cribl.cloud/api/assertIndex: Set this to
0.
Configure Attribute Statements
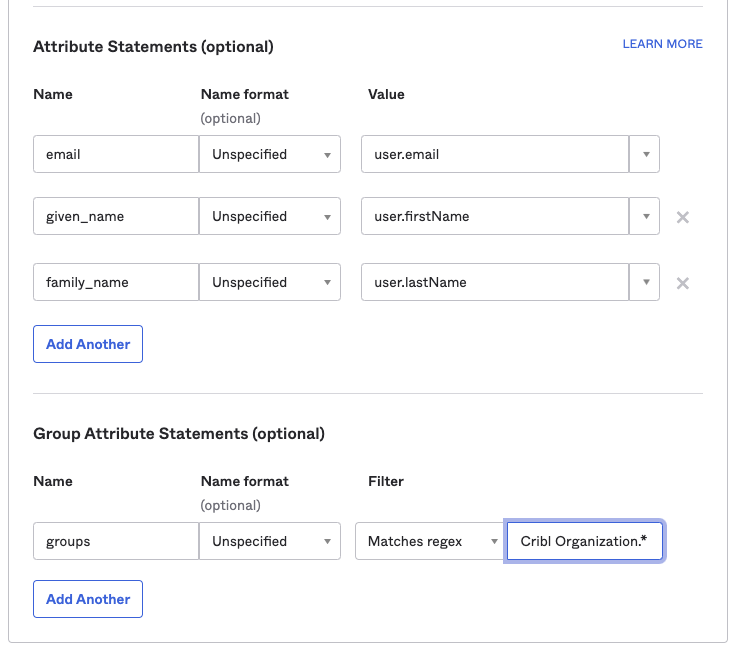
Configure Attribute Statements for these attributes, as shown below. Then save your app integration:
emailgiven_namefamily_namegroups
Submit Your App Info to Cribl
After you’ve created the SAML app integration in your IDP, provide Cribl essential metadata about your application, to implement SSO setup on the Cribl side.
On your Cribl.Cloud portal’s Organization page > SSO tab, select the SAML lower tab.
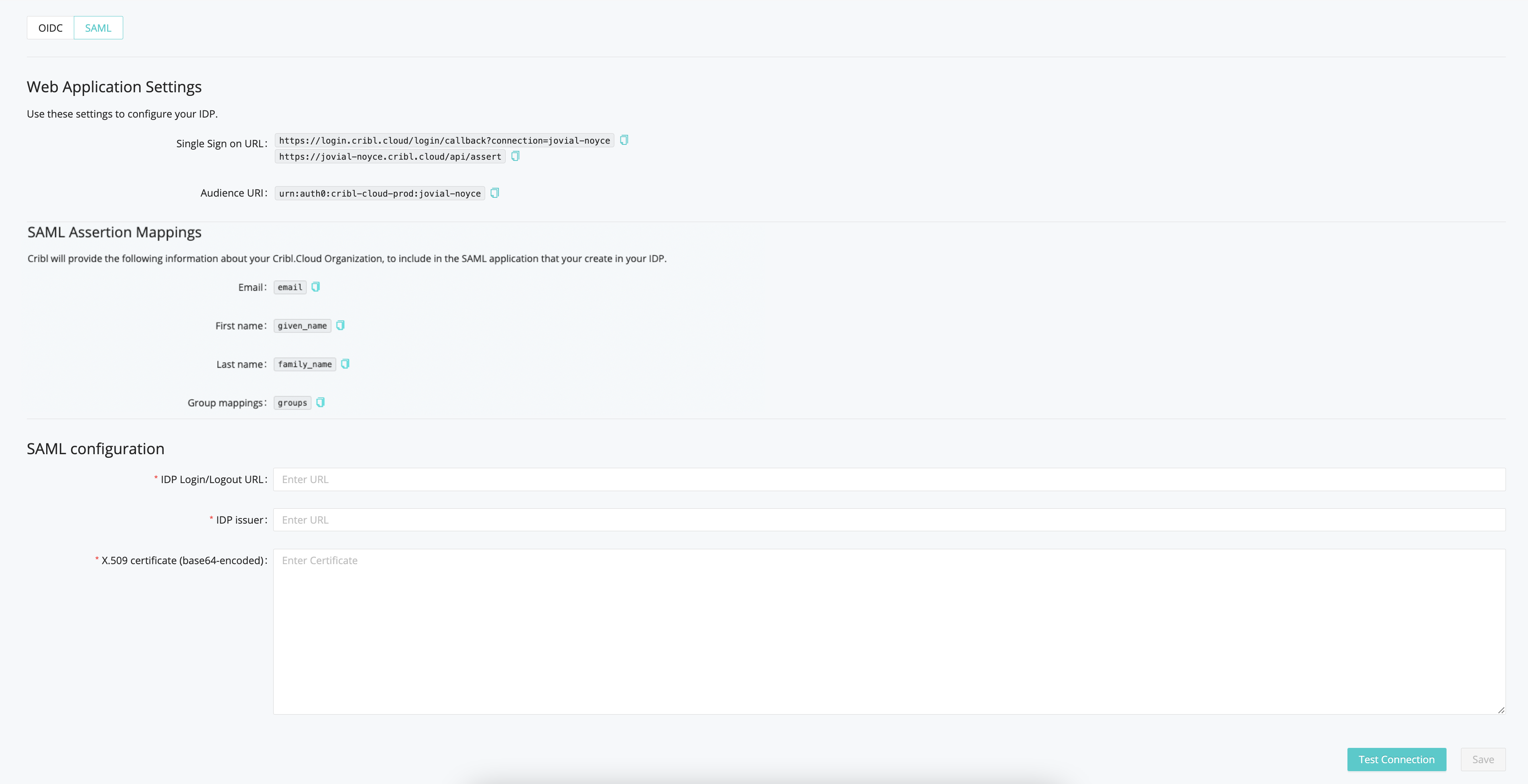
The Web Application Settings will be prefilled for you, and Cribl will also prefill the SAML Assertion Mappings based on the information you’ve registered with Cribl. So you only need to fill in the SAML Configuration section with the following details from your IDP client configuration:
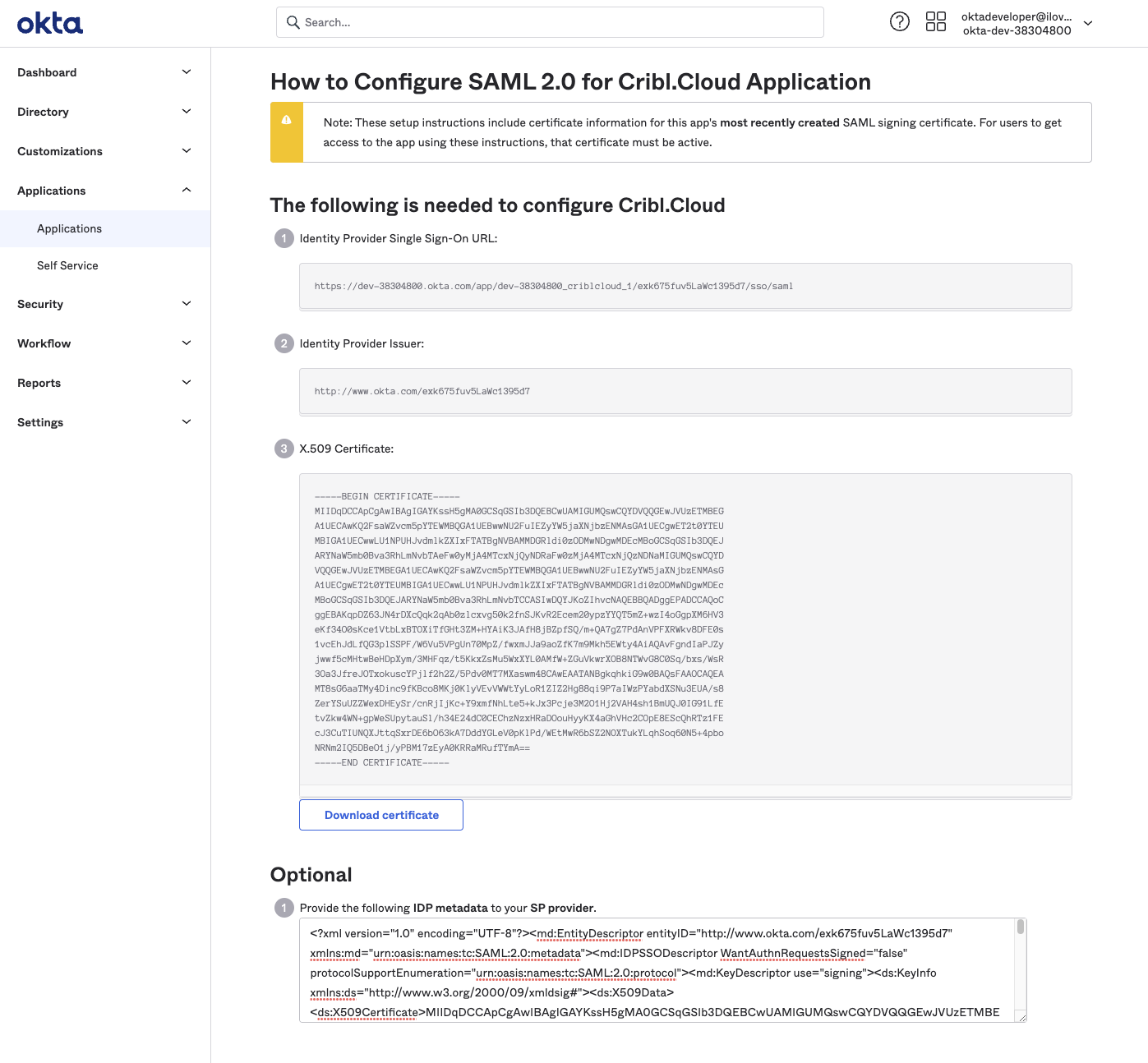
- IDP SSO
- IDP Issuer
- X.509 Certificate
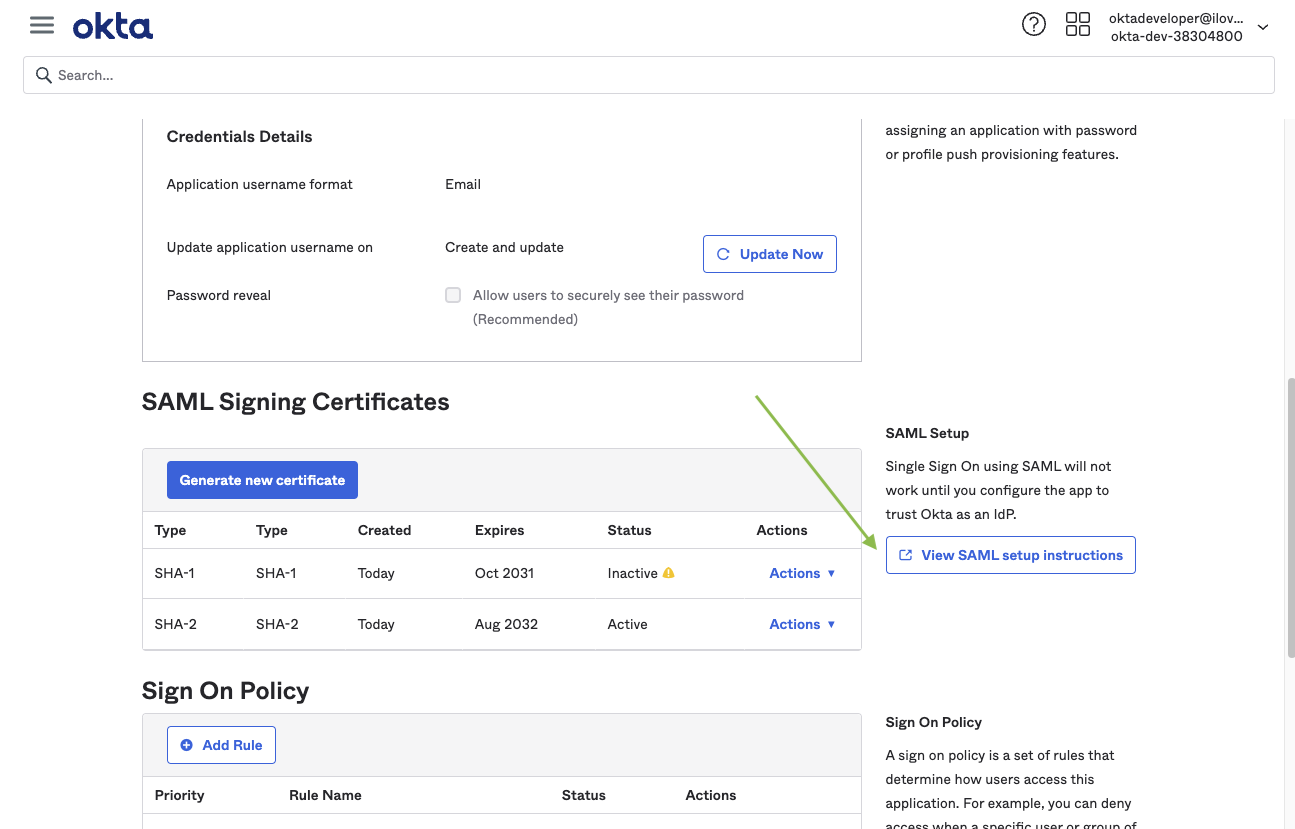
Continuing with our Okta example, these screenshots show how you’d export these metadata details from your Okta app:
SAML/Okta Chiclet Setup (Optional)
If you want to initiate login from your Okta instance with SAML authentication configured, an Okta admin can configure an app integration as follows:
From Okta’s left nav, select the Applications page.
Click Browse App Catalog.
From the resulting catalog, use the search bar to find and select the
Bookmark Appapplication.From that application’s page, click Add Integration.
On the General settings page, enter an Application label that will identify this app as supporting Cribl.Cloud login. (
Cribl.Cloudis a good choice, but the label is arbitrary.)In the URL field, enter
https://portal.cribl.cloud/login?connection=<organizationID>(where<organizationID>is your Cribl.Cloud Organization’s ID).
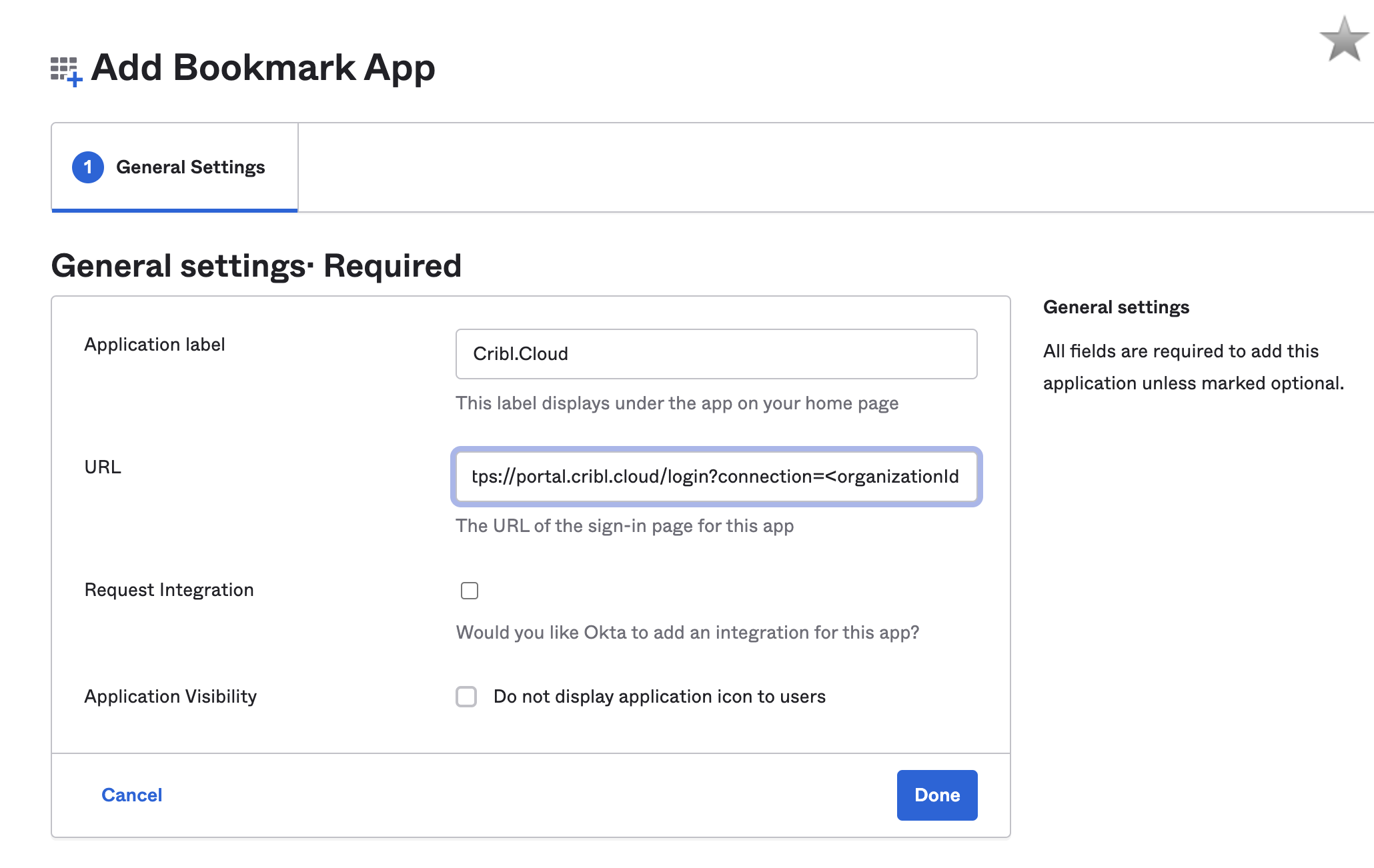
Click Done.
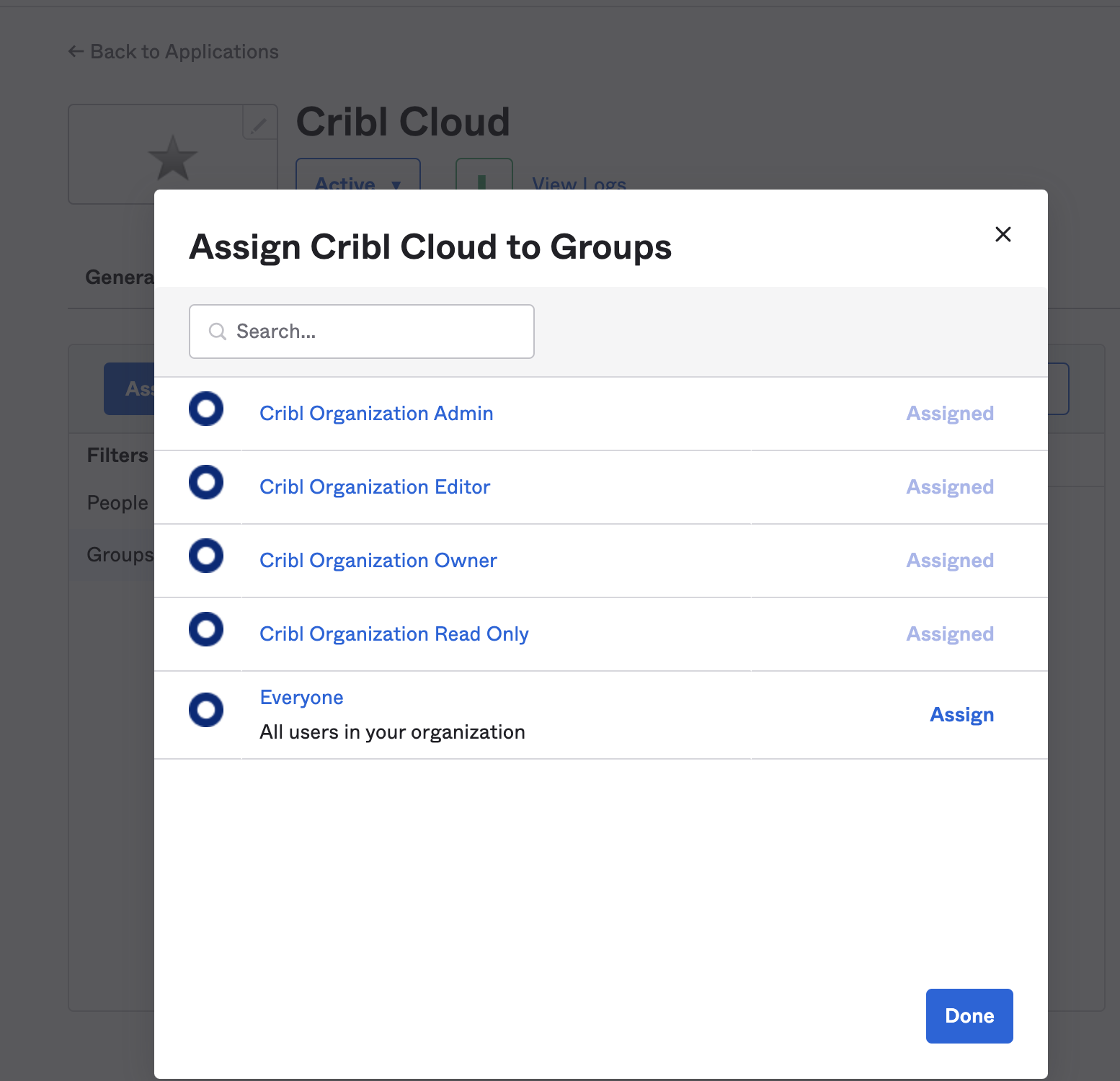
Click the Assign button, and assign all of the Cribl.Cloud groups to the application.
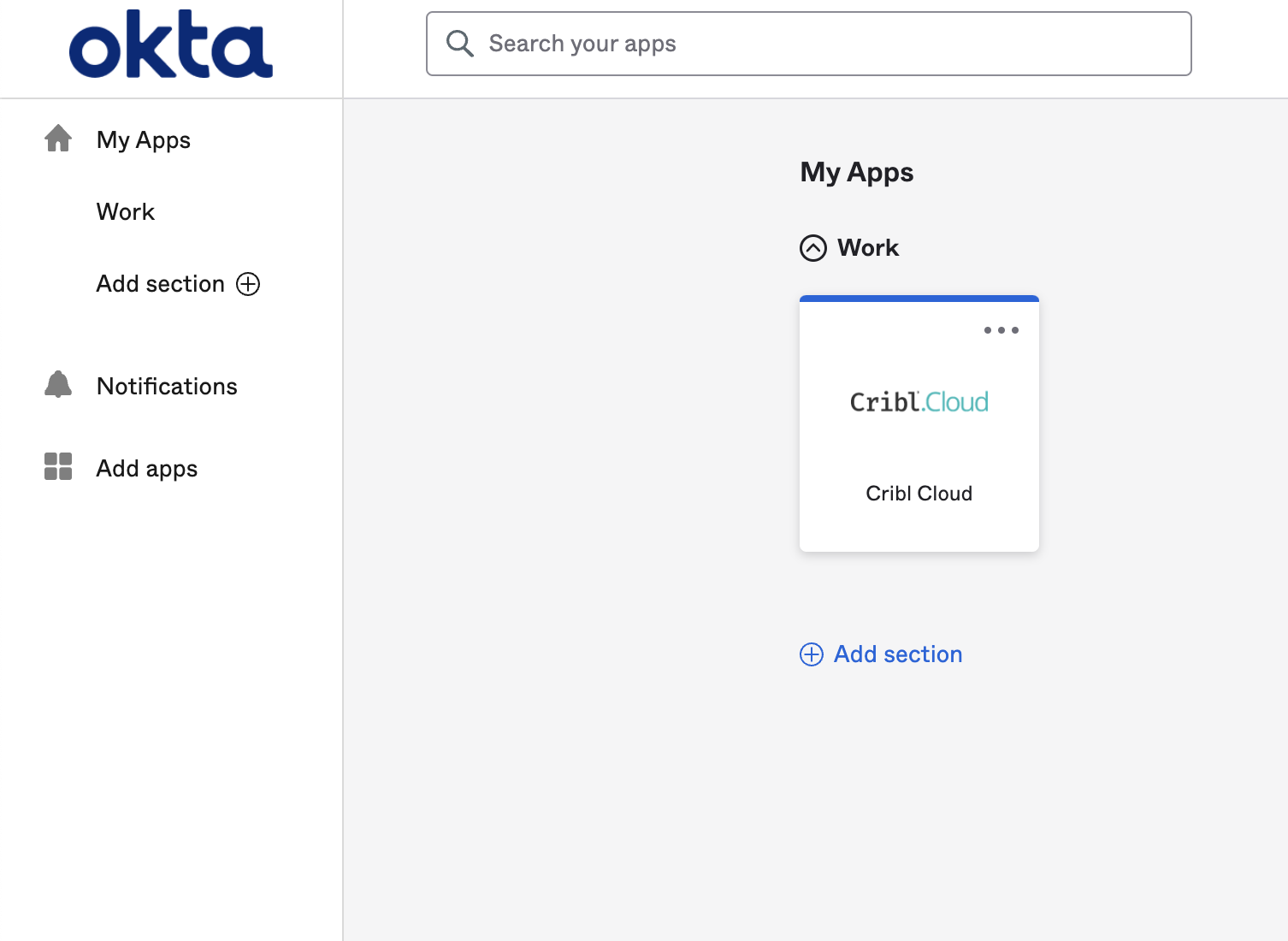
- The Cribl.Cloud chiclet should now be available for all users in the Cribl groups you’ve assigned.
Link Existing Users
To ensure that your Cribl.Cloud Organization’s local users have a smooth transition to SSO, see Final SSO Steps & Troubleshooting.





