These docs are for Cribl Stream 4.8 and are no longer actively maintained.
See the latest version (4.16).
SSO with Okta and OIDC (On-Prem)
Cribl Stream supports setting up SSO using OIDC to provide user authentication (login/password) and authorization (by mapping SSO users to Cribl Roles).
This page presents a walkthrough of setting up an OIDC SSO, using Okta as the example.
If you’d prefer to learn this information in the form of a video course, take a look at Cribl University’s Troubleshooting Criblet on SSO Integration for Stream On-Prem - Okta. The course walks you through a configuration flow of SSO wth Okta and OIDC. (To follow the direct course link, first log into your Cribl University account - it’s free!)
This page is a guide for configuring SSO for an on-prem installation. For Cribl.Cloud, see SSO with Okta and OIDC (Cribl.Cloud).
Ensure Fallback Access
To ensure fallback access for local users if SSO authentication fails, enable local authentication.
- Go to Global Settings.
- Under Access Management select Authentication.
- Toggle Allow login as Local User to Yes to allow users to log in using Cribl local authentication.
This enables an extra button called
Log in as Local Useron the login page.
To prevent lockout, Cribl strongly recommends enabling Allow login as Local User until you’re certain that external auth is working as intended. If you do get locked out, see Manual Password Replacement.
Create OIDC App Integration
To create your app integration:
In Okta, navigate to the Applications section and select Create App Integration.
Configure the app integration with the options below:
- Sign-in method:
OIDC - OpenID Connect - Application type:
Web Application
- Sign-in method:
Proceed with Next.
General Settings
- Configure the app integration’s General Settings with the options below:
| Setting | Description |
|---|---|
| App integration name | Your application name. |
| Logo | (Optional) Upload the Cribl logo. You can use a logo from the Cribl Press Kit. |
| Sign-in redirect URIs | Your Leader base URL, and with /api/v1/auth/authorization-code/callback as the path. |
| Sign-out redirect URIs | (Optional) Append /login to the pre-filled path. |
Assignments
In the Assignments pane, configure the access granted to Okta users:
To grant access to Cribl Stream to all Okta users, select Allow everyone in your organization to access.
To grant access to Cribl Stream to specific Okta groups, select Limit access to selected groups. Then, in the field below, add the groups you want to include.
After you finish creating the app, if you need to add or remove groups, do that in the Applications > Assignments tab.
Save your application.
In the Client Credentials panel, note down Client ID and Client Secret. You will need them in the next step.
Submit Your App Info to Cribl
Next, provide Cribl with essential details about your application to implement the SSO setup on the Cribl side.
In Cribl Stream, select Settings in the top nav, then in Access Management choose Authentication.
From the Type dropdown, choose
OpenID Connect.In the Provider name dropdown, select
Okta.In the Audience (Relying Party ID) field, enter your Cribl Stream UI base URL.
If you have a Distributed deployment with a fallback Leader configured, modify the Audience (Relying Party ID) field to point to the load balancer instead of the Leader Node.
In the Client ID and Client secret fields, enter the respective values that you copied from the Okta Client Credentials in the previous step.
If your Cribl Stream is in Enterprise Distributed mode:
In the Scope field, add the scope
groupsto the default space-separated list of scopes, so that it reads:openid profile email groups.
Get Okta App URLs
Next, get the authentication, token, userinfo, and logout URLs for your Okta app.
You can get them in JSON format from the /.well-known/openid-configuration endpoint:
https://<tenant>.okta.com/.well-known/openid-configuration
(<tenant> is your Okta tenant name). For example:
https://dev-12345678.okta.com/.well-known/openid-configuration.
You can use a tool like jq to automatically extract the URLs from the endpoint’s response with the following
curlcommand:curl -s https://<tenant>.okta.com/.well-known/openid-configuration | jq '. | {"auth": (.authorization_endpoint), "token":(.token_endpoint), "userinfo":(.userinfo_endpoint), "logout": (.end_session_endpoint)}'
Once you have the values, enter them in the respective fields in your Cribl Stream SSO configuration:
| Cribl Stream field | Okta URL |
|---|---|
| Authentication URL | authentication |
| Token URL | token |
| User info URL | userinfo. Fill it in if you configured Okta to use groups. |
| Logout URL | logout. Fill it in if you want Account > Log out in Cribl Stream to log the user out globally.This means that when a user selects the Accounts > Log out link in Cribl Stream, they are logged out of both Cribl Stream and Okta. |
Configure Response to Okta /userinfo Endpoint
An Okta tenant’s user groups can be mastered either inside Okta, outside Okta, or both.
When Cribl Stream queries the /userinfo endpoint, Okta returns the appropriate groups membership of the user.
See the Okta documentation on dynamic allow lists and using Okta together with Active Directory.
To configure this behavior, you need to set Groups claim type correctly, depending on where user groups are mastered.
- In Okta, go to your app and open the Sign On tab.
- In the OpenID Connect ID Token panel, select Edit
- Set Groups claim type to
Filter. - Choose Matches regex from the dropdown, and enter
.*as the regex.
Set Groups claim type to
Expression.In the Groups claim expression, enter an expression field that matches the groups you want passed to Cribl Stream.
For example, to match on Active Directory groups that contain the string
cribl, use the following expression:Groups.contains("active_directory", "cribl", 10)
- Click Save.
Configure ID Token to Include Groups Claim
For Okta to recognize your groups, you must configure the ID token to include your groups claim:
- In Okta, open the Security > API page.
- In the Authorization Servers tab, click the edit (pencil) button for the desired Authorization Server.
- In the resulting page, select the Claims tab.
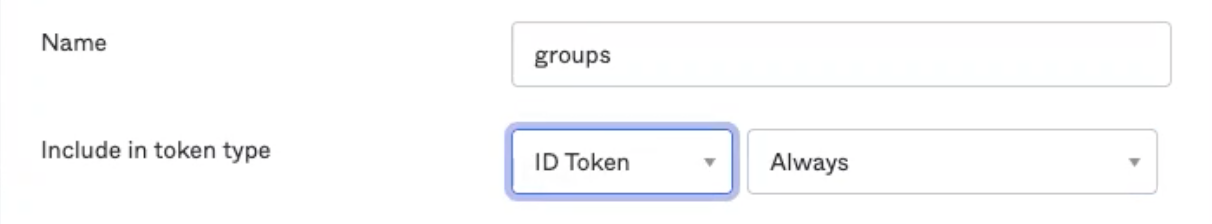
- If your groups claim already exists, click the edit (pencil) button. Otherwise, click Add Claim.
- In the Include in token type drop-downs, choose
ID TokenandAlways, respectively.
- Configure the remaining settings in the way that suits your groups claim.
- Click Save (or Create if you’re adding the claim for the first time).
Map Okta Groups to Cribl Stream Roles
Mapping groups to Roles is possible only for Cribl Stream deployments that are in Distributed mode, with an Enterprise license.
With a Standard license, all your external users will be imported to Cribl Stream in the admin role.
If you are running Cribl Stream in Single-instance mode, you cannot map Okta groups to Cribl Stream Roles, although you can still set up SSO with Okta.
As you think through how best to map your Okta groups to Cribl Stream Roles, keep these principles in mind:
- An Okta group can map to more than one Cribl Stream Role.
- A Cribl Stream Role can map to more than one Okta group.
- If a user has multiple Roles, Cribl Stream applies the union of the most permissive levels of access.
- Cribl Stream automatically assigns the
defaultRole to any user who has no mapped Roles.
For details on mapping your external identity provider’s configured groups to corresponding Cribl Stream user access Roles, see External Groups and Roles.
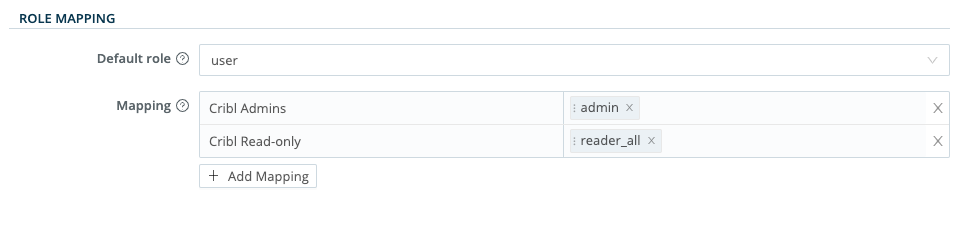
You can assign a Cribl Stream Role to each Okta group name, and you can specify a default Role for users who are not in any groups.
In Cribl Stream, select Settings, go to Access Management and then select Authentication.
Scroll down to the ROLE MAPPING section.
Cribl recommends that you set the
defaultRole touser, meaning that this Role will be assigned to users who are not in any groups.Add mappings as needed.
The Okta group names in the left column are case-sensitive, and must match the values returned by Okta (those you saw earlier when configuring Okta and OIDC).
Verify that SSO with Okta Is Working
- Log out of Cribl Stream, and verify that Okta is now an option on the login page.
- Select Log in with Okta.
- You should be redirected to Okta to authenticate yourself.
- The OpenID connect flow should complete the authentication process.
Get Temporary Access Credentials for AWS S3 Buckets
You can use your SSO/OIDC IDP to issue temporary access credentials so your on-prem Worker Node can access AWS S3 buckets.
Set the AWS_WEB_IDENTITY_TOKEN_FILE environment variable. This variable defines a path to a file that contains the OAuth/OIDC provided by the SSO IDP. You’ll also need to define AWS_ROLE_ARN and AWS_ROLE_SESSION_NAME.
You can use curl/Postman to make the required API calls.





