Workspaces
Workspaces offer a multi-tenancy capability, enabling you to create multiple isolated instances in your Cribl.Cloud Organization. This lets you strengthen your security, and fulfill compliance and isolation requirements.
Each Workspace offers a dedicated virtual private cloud (VPC) that acts as a separate environment within your Organization. Workspaces do not share product configurations, resources, or data flows, and each has a separate Leader Node. They do share a layer of access control (Organization-level Permissions and SSO configuration), as well as API credentials, licenses, and billing.
A centralized interface allows you to manage all your Workspaces and control access for Members and Teams to individual Workspaces.
Multiple Workspaces require a Cribl.Cloud Enterprise plan. For details, see Pricing.
An example use case scenario for creating multiple Workspaces is setting up separate environments for different business units in an enterprise. Data management, security, development, and any other units can have their own federated Workspaces, with completely separate members and permissions lists. This way, they can work in isolation without risk of interference and with increased focus.
Limitations
You can create up to 5 Workspaces per Organization.
If you need more Workspaces in your Organization (up to 50), contact Cribl Support to discuss extension options.
Multiple Workspaces require a Cribl.Cloud Enterprise plan. For details, see Pricing.
View Workspace Details
Workspaces provide a set of information that you can use when configuring data flow through their Worker Nodes.
View Access Details
To view detailed access information of your Workspace, in the sidebar, select Workspace and then Access.
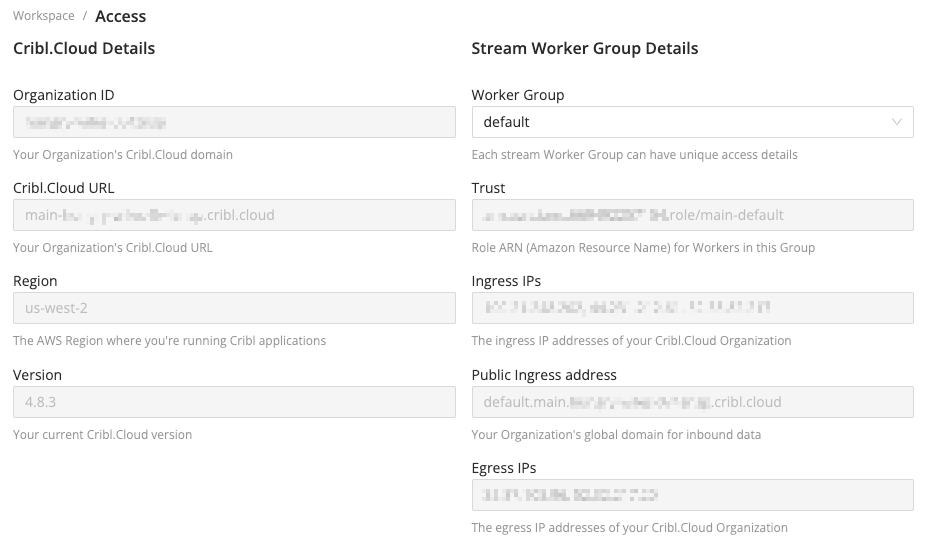
This page presents a summary of information about your Cribl.Cloud Organization, as well as the Cribl.Cloud URL for the current Workspace.
Cribl.Cloud URL
Cribl.Cloud URL is a static address associated with the load balancer that is in front of the Leader. Customer-managed (hybrid) Worker Nodes will connect to this address on port 4200, while the Leader UI is served from this address on port 443.
You can use this URL for certain API calls and certain Collection operations coordinated by the Leader.
Static External IPs for the Leader
The Leader NLB IPs field in Workspace > Access lists the IPs for the Leader Network Load Balancers associated with the Workspace.
Typically, only 2 of the 3 addresses will be active (returned by DNS) at any time, while the inactive address is swapped in during infrastructure maintenance events.
You can add all those IPs to your firewall allowlist to ensure that the load balancers are accessible across your hybrid deployment.
Stream Worker Group Details
Stream Worker Group Details provides information about Cribl-managed Worker Groups in Cribl.Cloud, if any are provisioned.
If no Worker Group is provisioned, you can select Provision Now to provision infrastructure for the Group. After a lag, the Group will be ready to process data, and this modal’s remaining fields will populate.
For a provisioned Worker Group, you see the following information:
| Field | Description |
|---|---|
| Trust | AWS IAM role ARN for Cribl-managed Workers in this Worker Group. Use this ARN as the principal in AWS trust policies when configuring cross-account access. |
| Ingress IPs | The IPv4 addresses of Worker Groups’ load balancers, also used when receiving data from Push Sources. These addresses will remain constant, so you can build firewall rules around them. Three Ingress IPs are provided for each Worker Group, one on each Availability Zone, assuming the Group has at least three Workers. In a Worker Group of fewer than three Workers, one of the IPs will be inactive. |
| Public Ingress address | Each Group’s domain for inbound data. This address prepends the Group name to the Organization’s global domain name. It does not append ports per data type - you can obtain these from the Data Sources tab. |
| Egress IPs | Your Cribl.Cloud Organization’s current public IP addresses. These addresses are Group-specific and also dynamic: Cribl will occasionally update them when we need to rescale core infrastructure. |
Public Ingress address and Egress IPs are used for both outbound connections from the Workers and Pull Sources.
Because individual Ingress IPs can become inactive, Cribl recommends that you send your data to the Public Ingress address instead of directly to IPs.
Egress IPs are not static.
If you need a static egress IP, contact Cribl Support.
Configuring Stream Groups (beyond the
defaultGroup) requires a certain plan. For details, see Pricing. For details about creating and provisioning Groups, see Cribl.Cloud Worker Groups.
View Data Sources
To view detailed access information about a Workspace’s Data Sources, in the sidebar, select Workspace and then Data Sources.
The Data Sources page lists ports, protocols, and data ingestion inputs that are open and available to use, including pre-enabled Sources. Use the Group drop-down to filter these details per Cribl-managed Worker Group in Cribl.Cloud. For details, see Available Ports and TLS Configurations.
For each existing Source listed here, Cribl recommends using the preconfigured endpoint and port to send data into Cribl Stream.
Get ARN
To get the Worker role ARN for a Workspace, in the sidebar, select Workspace. In the Stream Worker Group Details section, select a Worker Group and copy the value of the Trust field.
You can use this Worker ARN as the principal in the trust policy for an AWS account’s IAM role that Cribl Workers will assume. Attaching this trust relationship enables the AssumeRole action, providing cross-account access. For usage details, see the AWS Cross-Account Data Collection topic’s Account B Configuration section.
This option applies only to your Cloud Workers. You cannot use this technique to enable access to customer-managed hybrid Workers.
Set Up ACL
To set up Access Control List (ACL) Rules, in the sidebar, select Workspace and then Access Control List.
ACL Rules (IPv4 CIDR ranges) let you restrict data sent to your data sources. The Rules you define here are global to all Cribl-managed Worker Groups in Cribl.Cloud in the current Workspace. You can set up a maximum of 6 ACL Rules.
The default 0.0.0.0/0 rule (modifiable) imposes no limits.
End a rule with /32 to specify a single IP address, or with /24 to enable a whole CIDR block from x.x.x.0 to x.x.x.255.
Select Save after adding, modifying, or removing rules. Each change takes up to 5 minutes to propagate. During this time, rule editing is temporarily disabled to prevent conflicts. A successful update proceeds silently - you will not see a confirmation message.
The ACL options apply only to Cribl-managed Workers. You cannot use them to set access rules on customer-managed hybrid Workers.





